Simpl.AI
One PLATFORM Solution
Use Cases

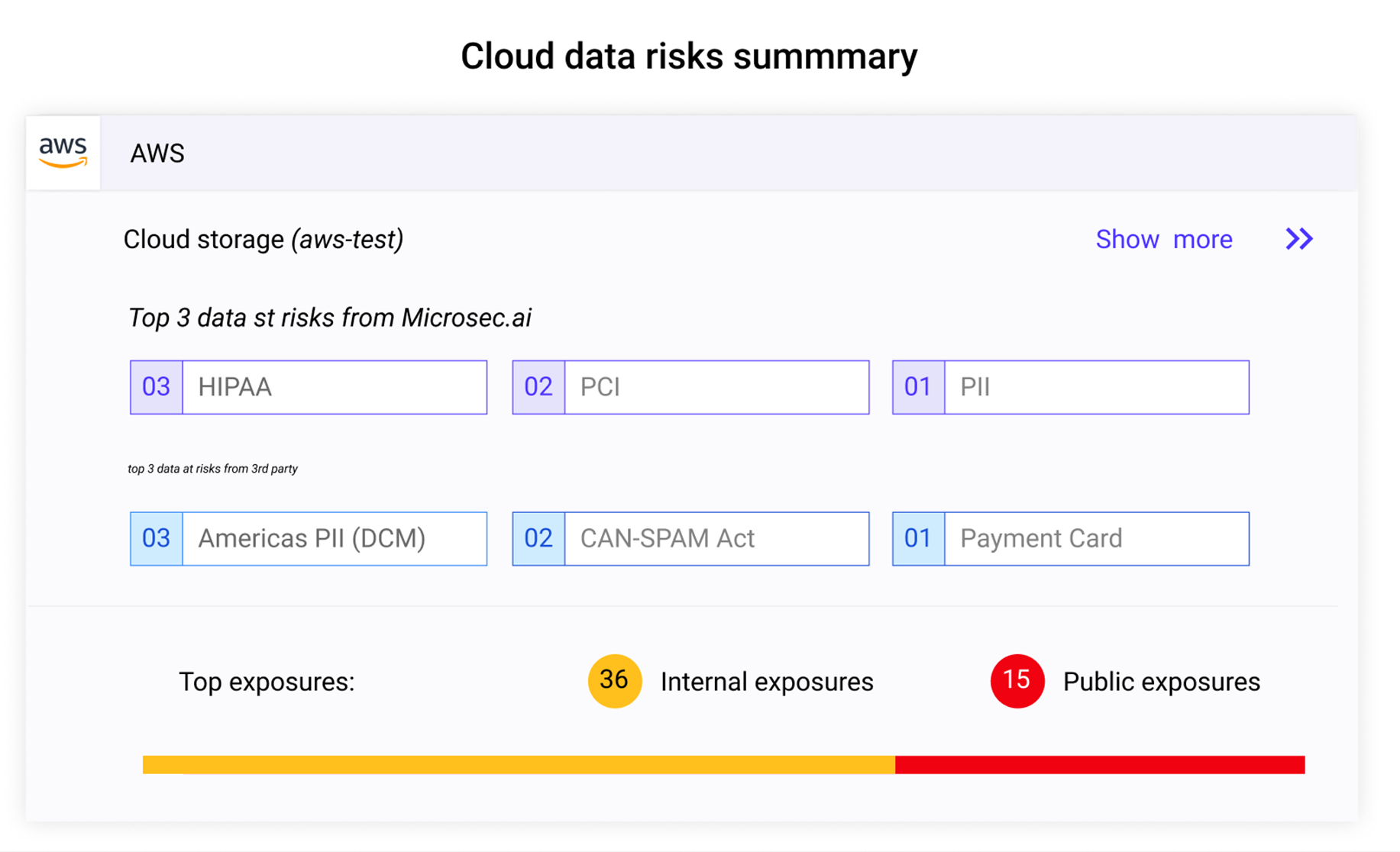
PREVENT CLOUD DATA BREACHES
Unprecedented visibility and runtime protection to eliminate data exposures. Remove risky access and control the spread of data.

ELIMINATE MISCONFIGURATIONS
Accidental misconfigurations are often exploited for successful cloud attacks. Automatically detect and eliminate these risks.

Vulnerability Management
Detect and patch vulnerabilities. Prioritize action with at-a-glance full security context.

Detect & Isolate Malware
Continuously scan for malware. Protect the cloud with policies to isolate or eliminate infected resources.

AUTOMATE COMPLIANCE
Easily monitor compliance, manage workflows, and collect evidence over time for CIS, PCI-DSS, NIST, SOC2, ISO 27001, and HIPAA.

Zero Trust
Know where all your confidential data is located. Exercise full control on access to both sensitive data and critical applications.

Data Privacy
Classify and track both sensitive data-at-rest and in-motion within cloud environments. Monitor encryption status and strictly control access.

Kubernetes Visibility & Control
Run-time visibility and control over network communications, data, vulnerabilities, and misconfigurations. Isolate risks and block imminent attacks.
INDUSTRY
TECHNOLOGY
FINANCE
HEALTHCARE
BLOCKCHAIN/CRYPTO
RETAIL
GOVERNMENT
Use Cases
PREVENT CLOUD DATA BREACHES
Unprecedented visibility and runtime protection to eliminate data exposures. Remove risky access and control the spread of data.
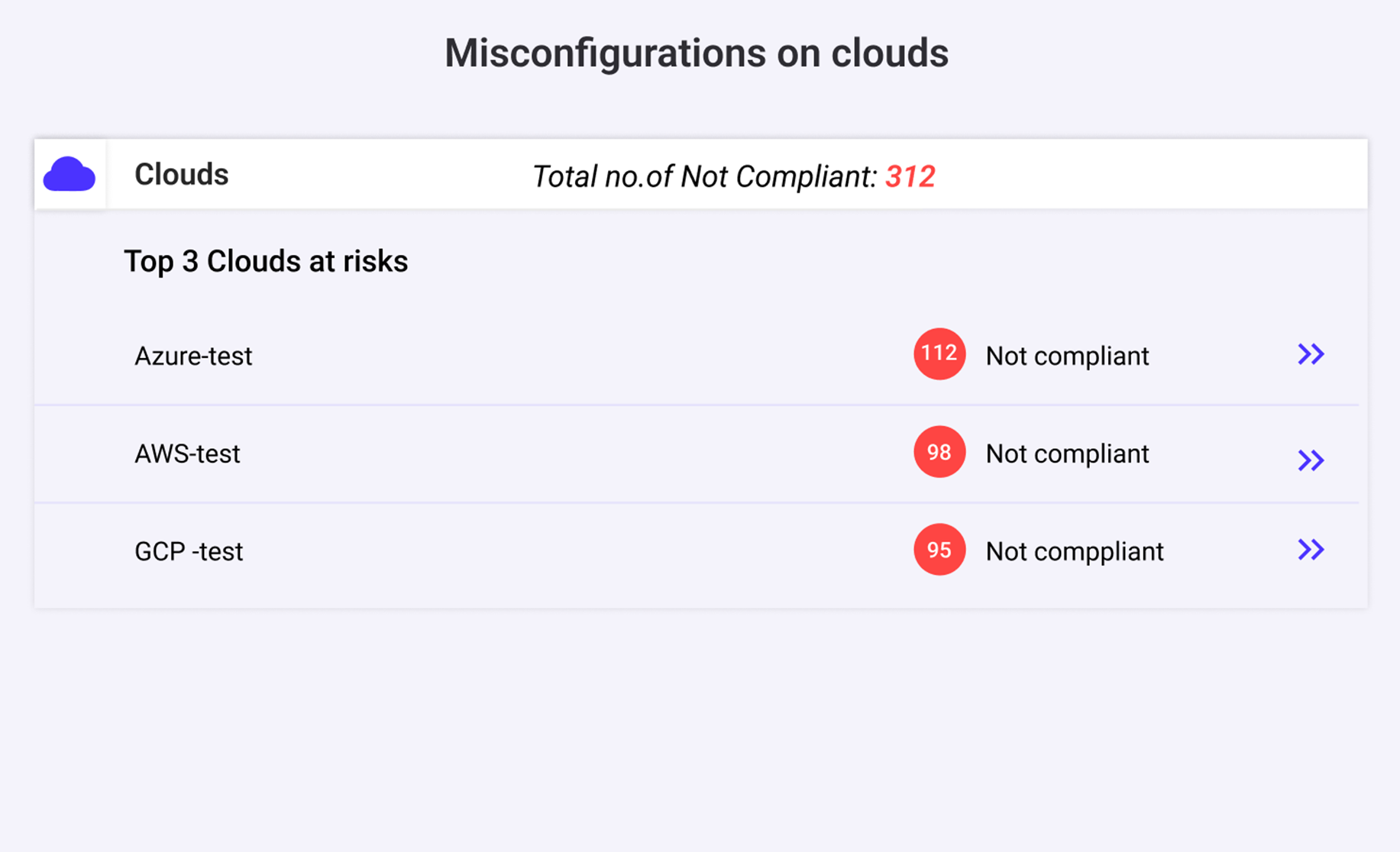
ELIMINATE MISCONFIGURATIONS
Accidental misconfigurations are often exploited for successful cloud attacks. Automatically detect and eliminate these risks.
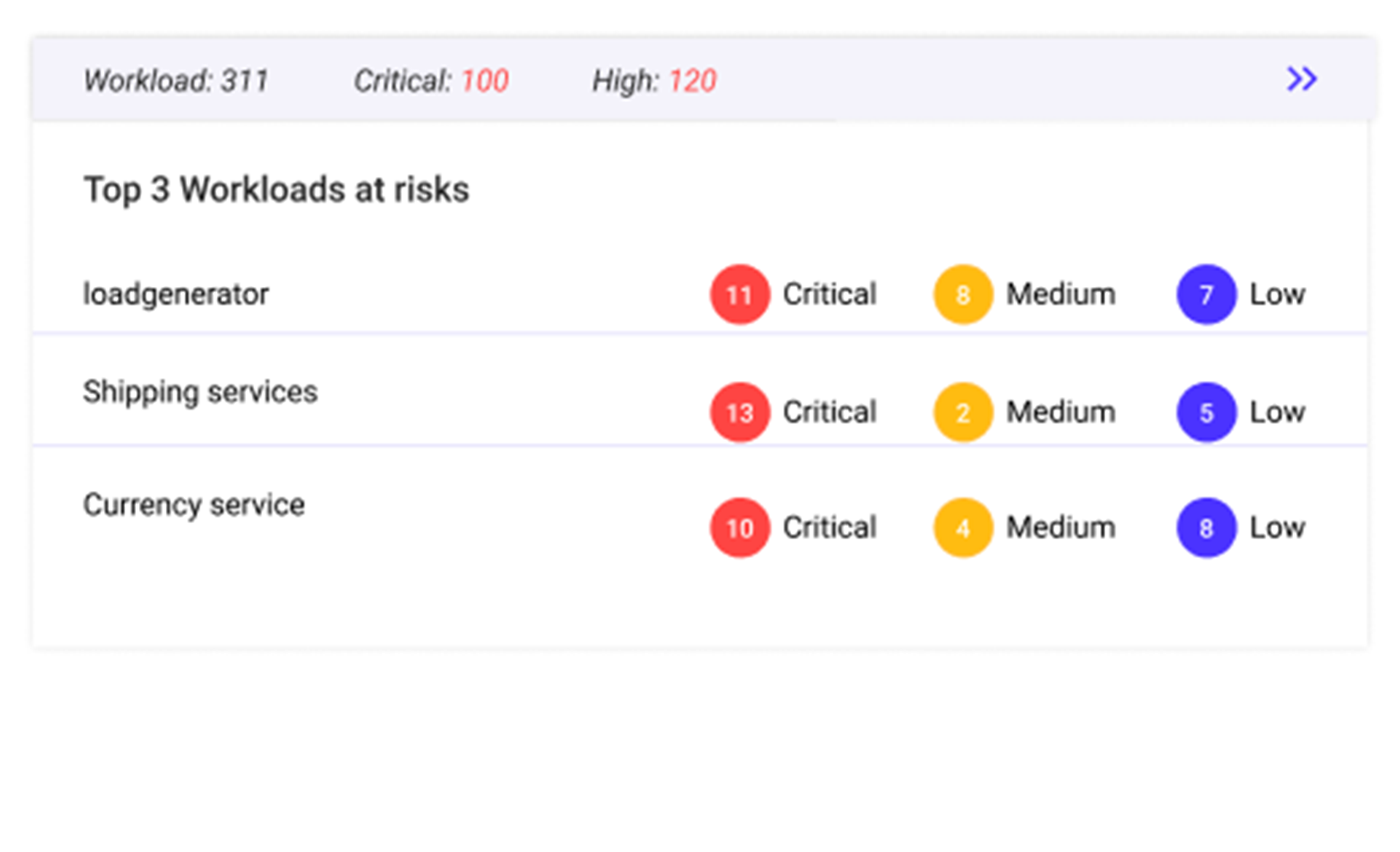
Vulnerability Management
Detect and patch vulnerabilities. Prioritize action with at-a-glance full security context.
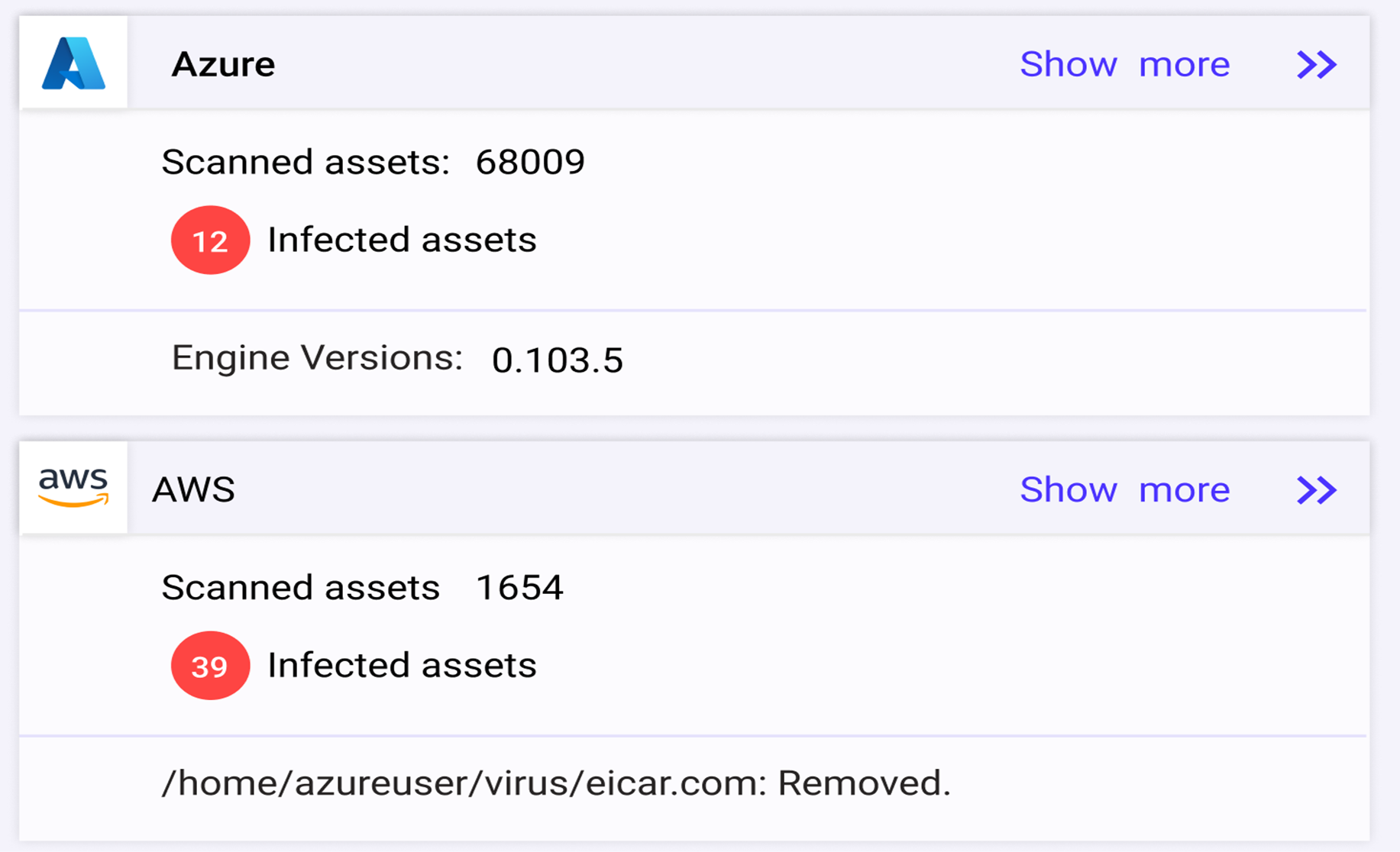
Detect & Isolate Malware
Continuously scan for malware. Protect the cloud with policies to isolate or eliminate infected resources.
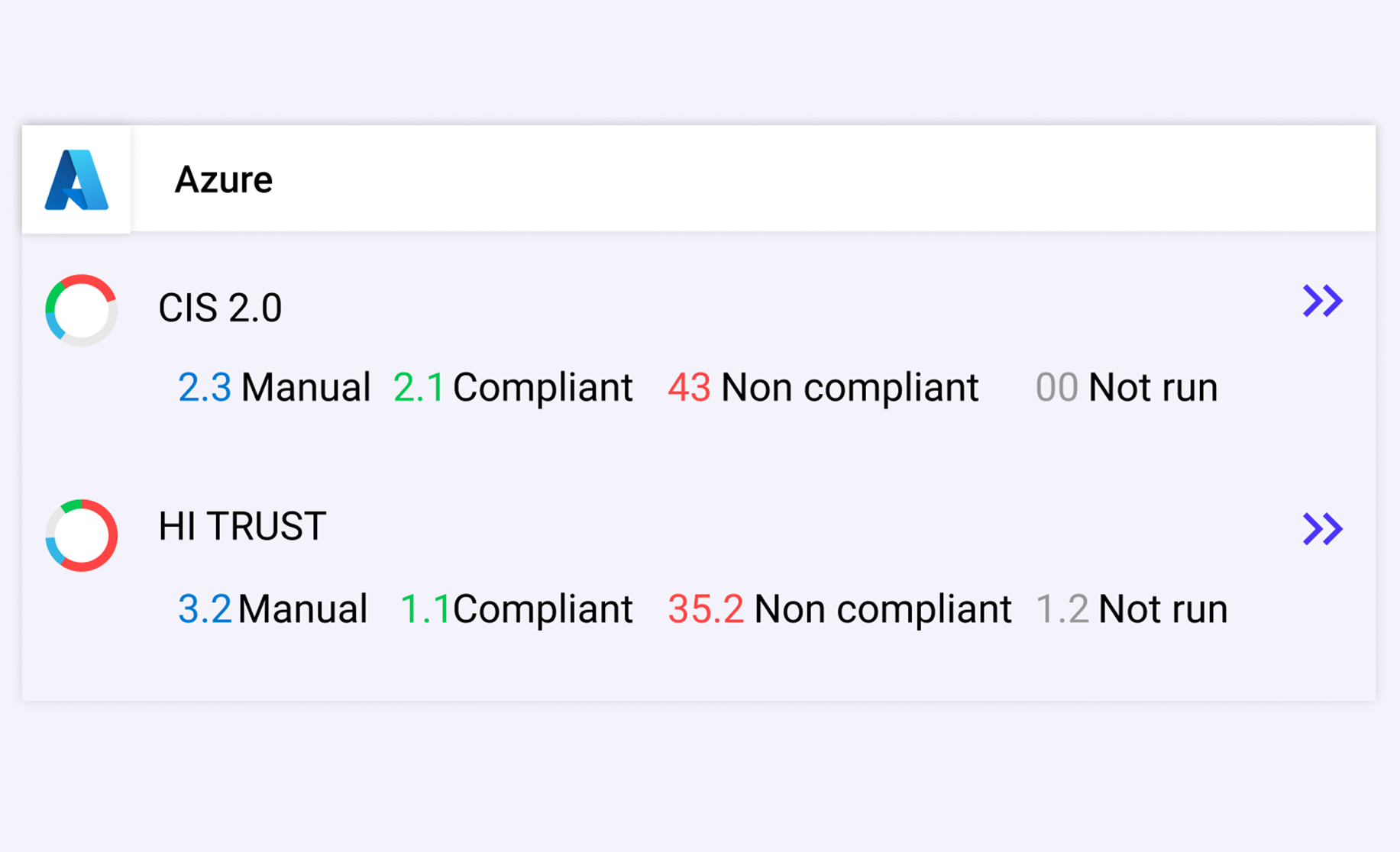
AUTOMATE COMPLIANCE
Easily monitor compliance, manage workflows, and collect evidence over time for CIS, PCI-DSS, NIST, SOC2, ISO 27001, and HIPAA.
Zero Trust
Know where all your confidential data is located. Exercise full control on access to both sensitive data and critical applications.
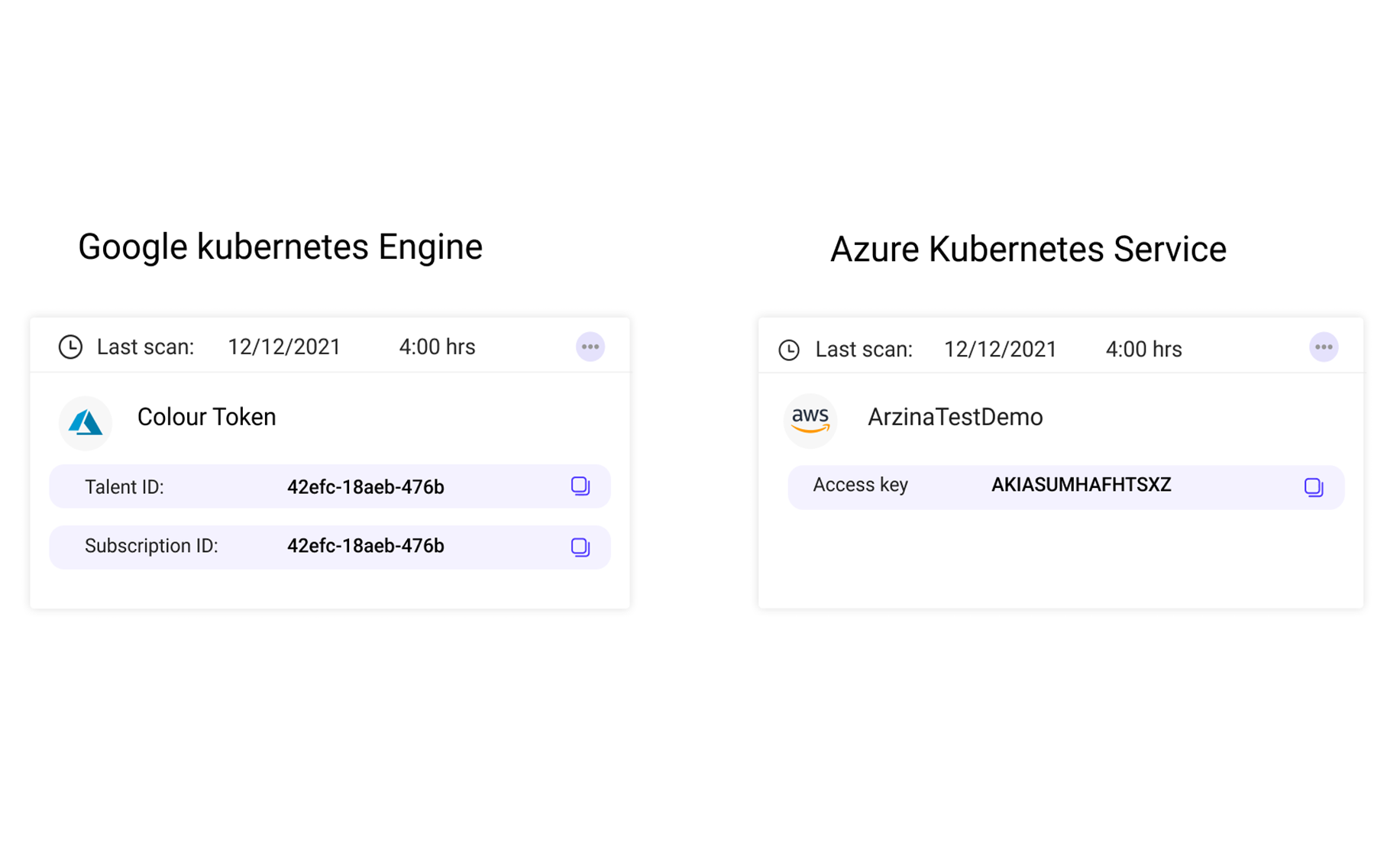
Data Privacy
Classify and track both sensitive data-at-rest and in-motion within cloud environments. Monitor encryption status and strictly control access.
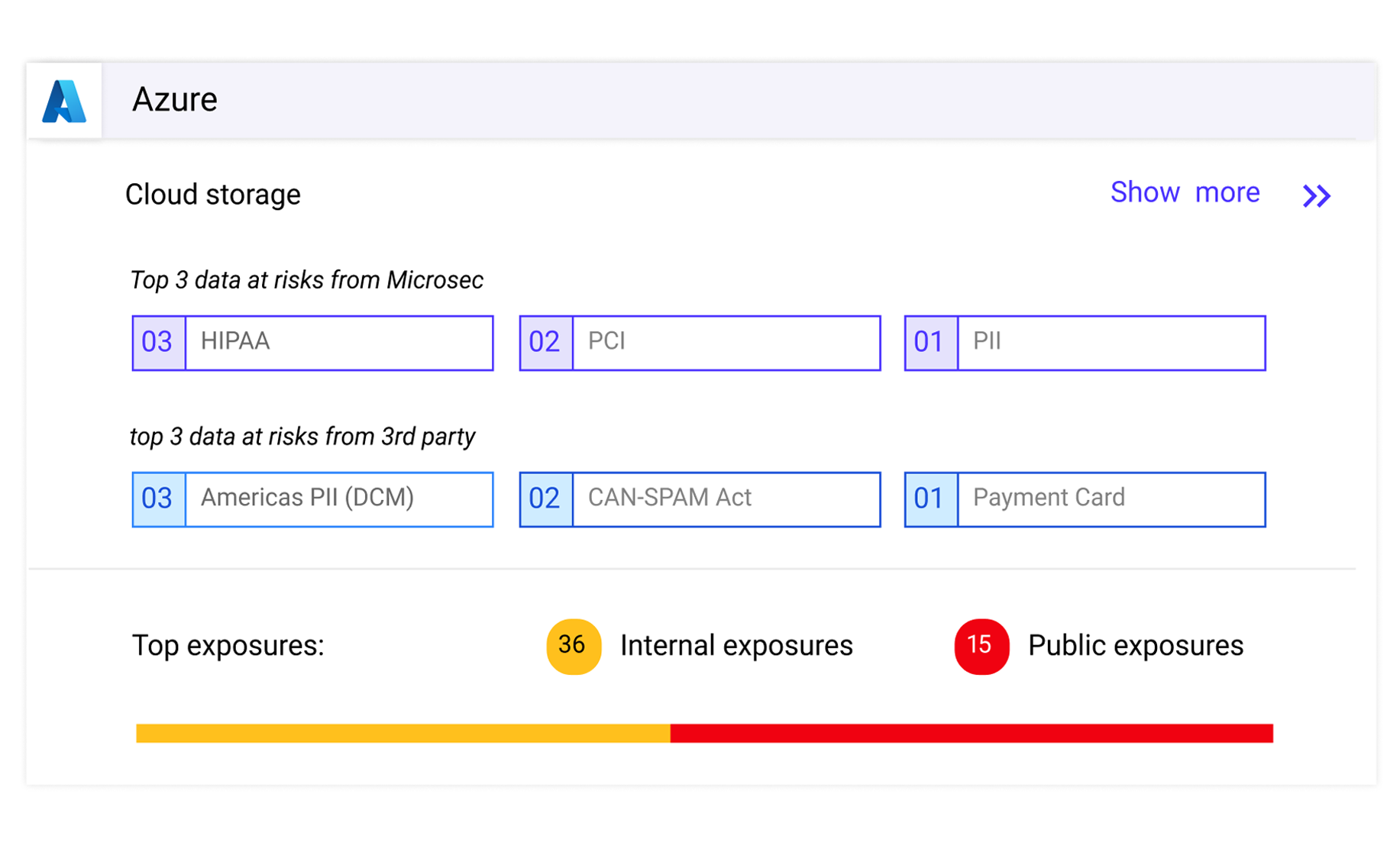
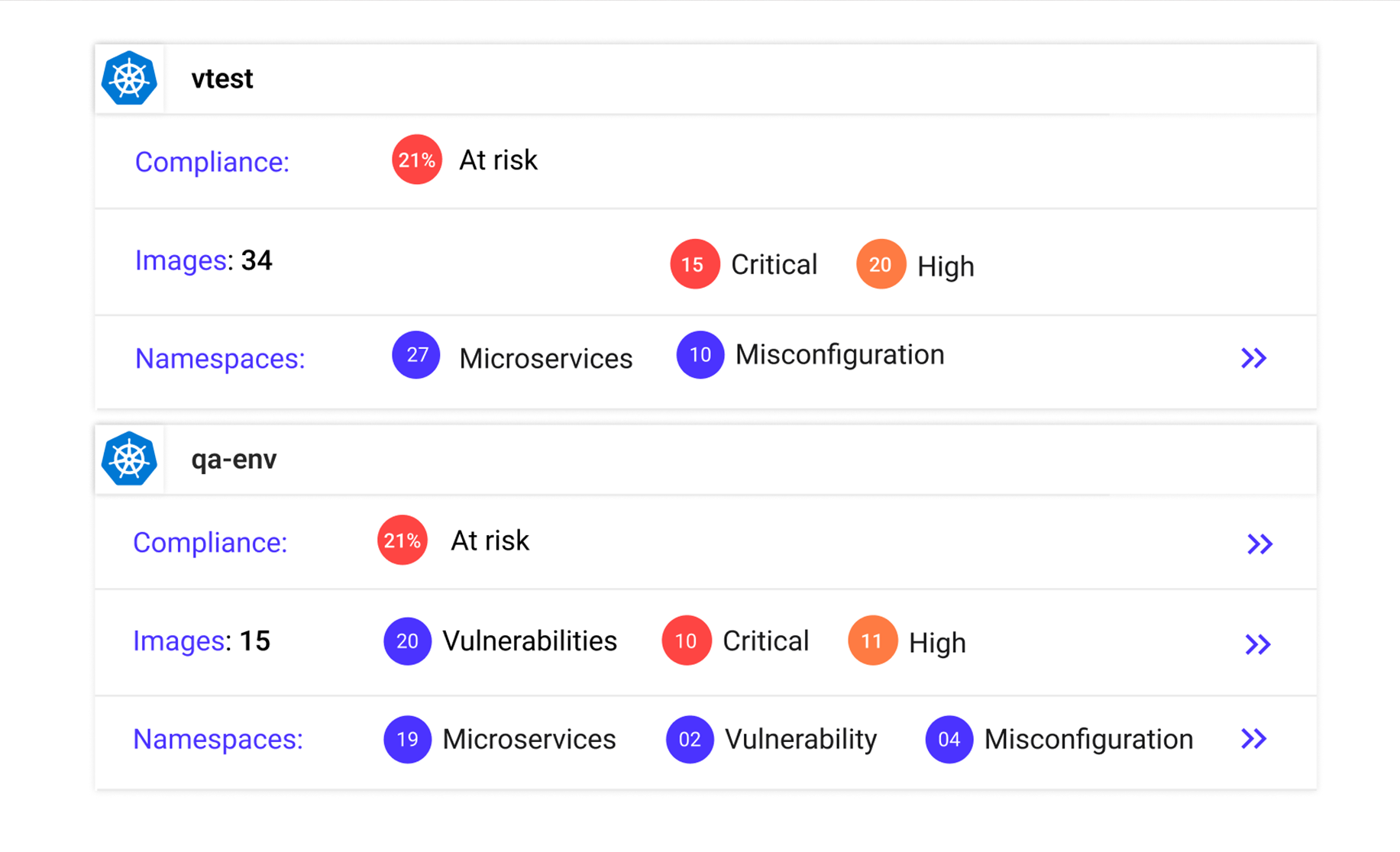
Kubernetes Visibility & Control
Run-time visibility and control over network communications, data, vulnerabilities, and misconfigurations. Isolate risks and block imminent attacks.
industry

Technology
Protect intellectual property and critical application availability with one unified solution. Optimal for multi-cloud environments or companies with a mix of traditional VM architectures and Kubernetes.

FINANCE
Save hundreds of hours by automating compliance work. Reduce financial risk by protecting valuable cloud data and applications against attack and exposure.
HEALTHCARE
Automate HIPAA and HITRUST compliance monitoring and evidence collection. Set policies to automatically protect healthcare data and applications against attack and exposure.

BLOCKCHAIN/CRYPTO
Reduce your security and financial risk by protecting the cloud applications that run your blockchain and the confidential data it contains.

RETAIL
Automate PCI-DSS compliance monitoring and evidence collection. Set policies to automatically protect customer data and cloud applications against attack and exposure.

GOVERNMENT
Protect confidential data and critical application availability with one unified solution.
finance

healthcare
Blockchain/crypto

Retail

Government

industry

FINANCE
Save hundreds of hours by automating compliance work. Reduce financial risk by protecting valuable cloud data and applications against attack and exposure.

HEALTHCARE
Automate HIPAA and HITRUST compliance monitoring and evidence collection. Set policies to automatically protect healthcare data and applications against attack and exposure.

BLOCKCHAIN/CRYPTO
Reduce your security and financial risk by protecting the cloud applications that run your blockchain and the confidential data it contains.

RETAIL
Automate PCI-DSS compliance monitoring and evidence collection. Set policies to automatically protect customer data and cloud applications against attack and exposure.

GOVERNEMNT
Protect confidential data and critical application availability with one unified solution.

Technology
Protect intellectual property and critical application availability with one unified solution. Optimal for multi-cloud environments or companies with a mix of traditional VM architectures and Kubernetes.
Technology

healthcare

Blockchain/crypto

Retail

Government

industry

HEALTHCARE
Automate HIPAA and HITRUST compliance monitoring and evidence collection. Set policies to automatically protect healthcare data and applications against attack and exposure.

BLOCKCHAIN/CRYPTO
Reduce your security and financial risk by protecting the cloud applications that run your blockchain and the confidential data it contains.

RETAIL
Automate PCI-DSS compliance monitoring and evidence collection. Set policies to automatically protect customer data and cloud applications against attack and exposure.

GOVERNMENT
Protect confidential data and critical application availability with one unified solution.

Technology
Protect intellectual property and critical application availability with one unified solution. Optimal for multi-cloud environments or companies with a mix of traditional VM architectures and Kubernetes.

FINANCE
Save hundreds of hours by automating compliance work. Reduce financial risk by protecting valuable cloud data and applications against attack and exposure.
Technology

finance

Blockchain/crypto

Retail

Government

industry

BLOCKCHAIN/CRYPTO
Reduce your security and financial risk by protecting the cloud applications that run your blockchain and the confidential data it contains.

RETAIL
Automate PCI-DSS compliance monitoring and evidence collection. Set policies to automatically protect customer data and cloud applications against attack and exposure.

GOVERNMENT
Protect confidential data and critical application availability with one unified solution.

Technology
Protect intellectual property and critical application availability with one unified solution. Optimal for multi-cloud environments or companies with a mix of traditional VM architectures and Kubernetes.

FINANCE
Save hundreds of hours by automating compliance work. Reduce financial risk by protecting valuable cloud data and applications against attack and exposure.

HEALTHCARE
Automate HIPAA and HITRUST compliance monitoring & evidence collection. Set policies to automatically protect healthcare data and applications against attack and exposure.
Technology

finance

healthcare

Retail

Government

industry

RETAIL
Automate PCI-DSS compliance monitoring and evidence collection. Set policies to automatically protect customer data and cloud applications against attack and exposure.

GOVERNMENT
Protect confidential data and critical application availability with one unified solution.

Technology
Protect intellectual property and critical application availability with one unified solution. Optimal for multi-cloud environments or companies with a mix of traditional VM architectures and Kubernetes.

FINANCE
Save hundreds of hours by automating compliance work. Reduce financial risk by protecting valuable cloud data and applications against attack and exposure.

HEALTHCARE
Automate HIPAA and HITRUST compliance monitoring and evidence collection. Set policies to automatically protect healthcare data and applications against attack and exposure.

BLOCKCHAIN/CRYPTO
Reduce your security and financial risk by protecting the cloud applications that run your blockchain and the confidential data it contains.
Technology

finance

healthcare

Blockchain/crypto

Government

industry

GOVERNMENT
Protect confidential data and critical application availability with one unified solution.

Technology
Protect intellectual property and critical application availability with one unified solution. Optimal for multi-cloud environments or companies with a mix of traditional VM architectures and Kubernetes.

FINANCE
Save hundreds of hours by automating compliance work. Reduce financial risk by protecting valuable cloud data and applications against attack and exposure.

HEALTHCARE
Automate HIPAA and HITRUST compliance monitoring and evidence collection. Set policies to automatically protect healthcare data and applications against attack and exposure.

BLOCKCHAIN/CRYPTO
Reduce your security and financial risk by protecting the cloud applications that run your blockchain and the confidential data it contains.

RETAIL
Automate PCI-DSS compliance monitoring and evidence collection. Set policies to automatically protect customer data and cloud applications against attack and exposure.
Technology

finance

healthcare

Blockchain/crypto

Retail

industry
Technology

finance

healthcare

Blockchain/crypto

Retail

Government

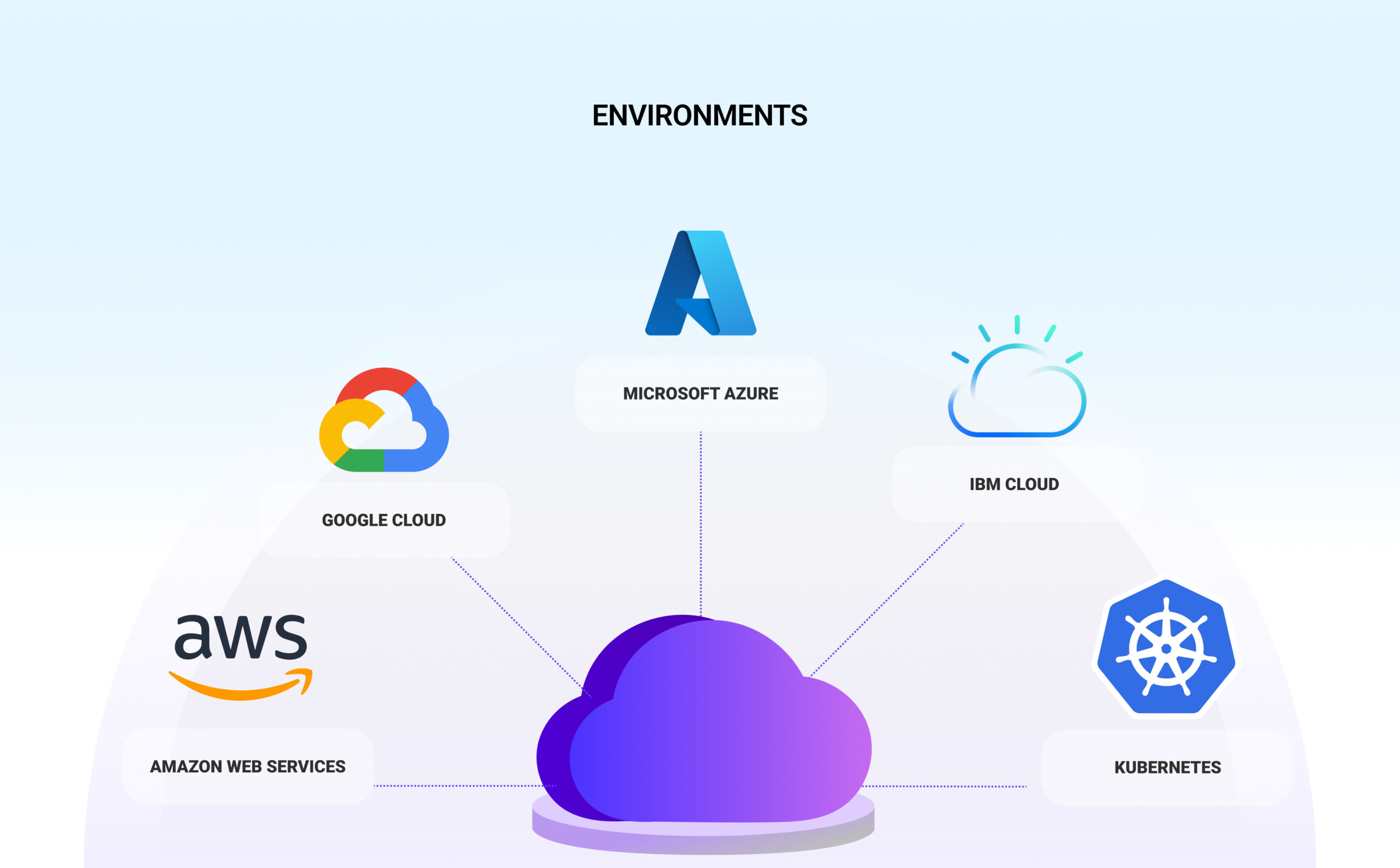
Environments